Strategic Legal Futures & Foresight
Strategic foresight is an organizational, social, and personal practice that allows us to create functional and operational views of alternative futures and possibilities.

FutureLaw.ai seeks to transform the next generation of lawyers to be more AI savvy and operate in an increasingly data driven AI economy.
It is an industry-based training platform to get legal professionals ready for Industrial Revolution 4.0.
Our Mission is to equip legal professionals with the knowledge and skills to deal with new technologies such as AI/Machine learning in law (including generative AI).
We focus on lawyering for the future data-driven AI economy!

* (including generative AI)


Zaid Hamzah
is an AI and data strategist and practitioner specializing in AI in law and finance, AI and data governance and AI in information security. An AI patent holder, he is currently an Executive Education Fellow at the National University of Singapore (NUS) School of Computing’s Advanced Computing for Executives centre where he runs programmes on AI Innovation Management, Intellectual Property Rights in AI Innovation, and Commercialisation of AI Innovation. He has taught legal AI at the Singapore Management University School of Law. Zaid is deeply involved in AI R&D and innovation. His AI patent relating to risk management in a supply chain context was granted by the Intellectual Property Office of Singapore in December 2023. He is currently involved in AI research and innovation in the area of decision intelligence and cybersecurity.
Author of 10 books spanning law, technology, intellectual property and AI, Zaid has over 35 years of professional experience. He has previously served as (i) Microsoft's Director for intellectual property and commercial software; (ii) Senior Legal Advisor to Singtel’s joint venture with Warner Bros and Sony Pictures; (iii) Chief Regulatory Legal & Compliance Officer at publicly-listed Telekom Malaysia; (iv) Associate, Khattar Wong & Partners (Singapore law firm) and (v) Singapore Government service. Zaid has a law degree from the National University of Singapore and completed his Masters in International Relations at the Fletcher School of Law and Diplomacy, Tufts University on a Fulbright scholarship.
Zaid is a member of the Board of Directors, NIE International (which is wholly owned by Nanyang Technological University). Zaid volunteers his professional services to start ups in the area of AI management and intellectual property protection and regularly conducts community programs on how to get young children ready for a data and AI future.


Explore our course offerings covering strategic legal futures & foresight,
AI/Machine learning in law (including generative AI), design thinking in law, smart city law,
cybersecurity law & compliance,
and public international law of cyberspace.
Strategic foresight is an organizational, social, and personal practice that allows us to create functional and operational views of alternative futures and possibilities.
Against the backdrop of Industrial Revolution 4.0, the legal industry is being disrupted by artificial intelligence.
Legal design thinking (LDT) is about taking a creative, experimental, and user-centered approach to how we provide legal services.
Smart city law is about the laws and regulations in the design and development of smart cities.
This course will equip students with the knowledge and skills to deal with cybersecurity attacks from the legal, investigative, risk management and policy aspects.
We provide training in strategic cybersecurity compliance risk management and compliance performance management.
This course examines the international legal regulation of both the conduct of States among themselves and conduct towards individuals, in relation to the use of cyberspace.
Strategic Legal Futures and Foresight (SLFF) is the application of strategic foresight in the legal sector for exploring possible or probable futures in the legal industry. Strategic foresight is an organizational, social, and personal practice that allows us to create functional and operational views of alternative futures and possibilities. With the integration of generative AI in law, particularly in areas such as Natural Language Processing (NLP), the SLFF program aims to leverage advanced technologies to enhance foresight capabilities.
Futures studies (colloquially called "futures") is the formal and systematic study of possible, probable, and preferable futures, incorporating cutting-edge methodologies including generative AI. This discipline explores methods of foresight development for individuals, groups, and human society, especially within the evolving landscape of legal technology.
Futures thinking is one of the most critical skill sets for organizational leadership today. We depend a lot on hindsight to run our businesses, economies and countries. In our rapidly changing world, this can no longer be our practice. Our leaders must develop the skill of identifying emerging issues, building alternative scenarios, and creating transformational futures, utilizing technologies such as generative AI for legal analysis.
The SLFF program is a crucial first step in developing foresight skills for legal professionals, especially strategic legal thinkers. Robust legal foresight, incorporating generative AI can be utilized to enhance the quality of strategic decision-making in the lawyering ecosystem, especially in complex industrial revolution 4.0 operating environments. This course will enable lawyers to implement legal foresight programs that leverage generative AI and NLP, improving their organization’s capacity to realize opportunities and manage both strategic and operational legal risks in this era of disruptive technological, economic, and social change.
Key Takeaways
At the end of the course, participants will be able to:
Who Should Attend
This programme has been designed for both lawyers as well as non lawyers who sit in Board of Directors, C-Suite Executives, Executive Leadership teams, Strategic/Transformation teams. Senior Management, and their teams who work on the development of strategic futures and foresight perspectives for their organisations will find this programme highly relevant.
The course is particularly relevant for those engaged in:
This executive program is relevant to both public and private sectors. Corporate runs can be customised to incorporate the topics and issues of specific interest to participants in industry.
Topics covered:
These topics will be covered in a 2-day, 16-hour programme blending theory, case study and practical workshop exercises that can be applied directly in the workplace.
It can be customised to accommodate the specific projects, topics or issues relevant to course participants. In this case, the workshop will focus on a set foresight project or challenge highlighted by participants, incorporating the use of generative AI in legal problem-solving.
Against the backdrop of Industrial Revolution 4.0, the legal industry is being disrupted by artificial intelligence (AI). Legal analytics and AI-driven applications in law are transforming the nature of legal service delivery globally. New forms of machine learning-driven legal services have emerged in emerging areas such as AI-enabled judicial analytics, compliance, and law enforcement analytics. How will all these affect legal professionals in the future?
In this program, course participants course participants will learn recent developments in the legal technology landscape and analyze the impact of machine learning in law, including generative AI in both legal practice as well as in corporate legal departments. The program will cover the use of Natural Langage Processing (NLP) / Large Language Model (LLM) in (i) the rise of contract analytics in the review of transactional documents (ii) regulatory analytics in the context of compliance (iii) judicial analytics or court analytics; and (iv) analytics tools for in-house legal teams that could optimize external counsel resource allocation, cost management, and internal productivity.
The program will peek into the future where law-related robo-advisory services based on machine learning (including generative AI) are likely to creep into the legal advisory universe through the deployment of algorithmic thinking, unsupervised machine learning, advanced analytics, and predictive coding. Course participants will learn how to manage emerging liability issues in the development of these cutting-edge technologies. How will these developments affect the role of in-house counsels and the role of lawyering in the future economy? This course will lay the foundation for lawyering in the technology-driven future economy.
Note: There are no pre-requisites to attend this course and no technical background is required.
Aims
This elective aims to provide course participants with knowledge of:
Learning Outcomes
On completion of this elective, course participants will:
Skills Outcomes
The course participants will:
Legal design thinking (LDT) is about taking a creative, experimental, and user-centered approach to how we provide legal services. It is about taking the same design process taught in design school and applying it in the legal context. LDT takes a human-centered approach and applying it to the world of law to benefit individual clients and eventually benefitting society.
The aim of LDT is to get students and practitioners to develop real solutions to real problems and to learn to view a legal challenge in a new way. The basic principle of LDT is to try to make the law more accessible to individuals who are not trained in law. Effective LDT should help solve specific legal problems. Beyond focusing on the substantive aspects of the law, LDT is primarily about presenting legal issues in an understandable way to clients.
LDT offers a technique that can be used in practice and have many applications in all areas of lawyering that ultimately seeks to advance the interests of the clients. In LDT, unlike traditional law classes, you must focus on the user problems first, as opposed to starting from a macro-view of what the law is. It has to be hands on and you will need to focus on the client’s perspectives first.
Course Outline
Smart city law is about the laws and regulations in the design and development of smart cities.
A smart city is a term given to a city that incorporates information and communication technologies (ICT) especially sensor technology and big data analytics to enhance the quality and performance of urban services. Such urban services include energy, transportation and utilities in order to reduce resource consumption, wastage and overall costs.
The overarching aim of a smart city is to enhance the quality of living for its citizens through smart technology and the sustainable use of resources. Smart city laws are the laws and regulations that govern the design, development and maintenance of smart cities.
This course comprises the following modules:
The phenomenal growth of the networked environment, the increase in the number of malicious cyberattacks and the heightened risk of cyberterrorism against critical information infrastructures (such as national power grid, transportation, health, banking and finance infrastructure) have made cybersecurity a critical national agenda. Cyberattacks harm national security and business interests and are considered as criminal acts in most jurisdictions. In dealing with cybersecurity attacks, understanding how the law and legal processes operate is a critical and unavoidable aspect. Beyond cybercrimes, broader cybersecurity concerns such as cyberattacks from nation states and non-state actors have emerged.
With cyberterrorism and state sponsored cyberintelligence activities on the rise, cyberdefence has become a new strategic imperative. With traditional geopolitical risks increasingly layered with cybersecurity risks, international relationship management now requires new forms of cooperation between states in the new cyberworld. At the enterprise level, the establishment of a robust legal risk management framework and prosecution regime to fight cybercrime and cyberterrorism continues to be an essential building block. Enterprises, governments and other organizations needs to create a proactive and structured legal and regulatory risk management framework to better manage cybersecurity risks and ensure cybersecurity resilience.
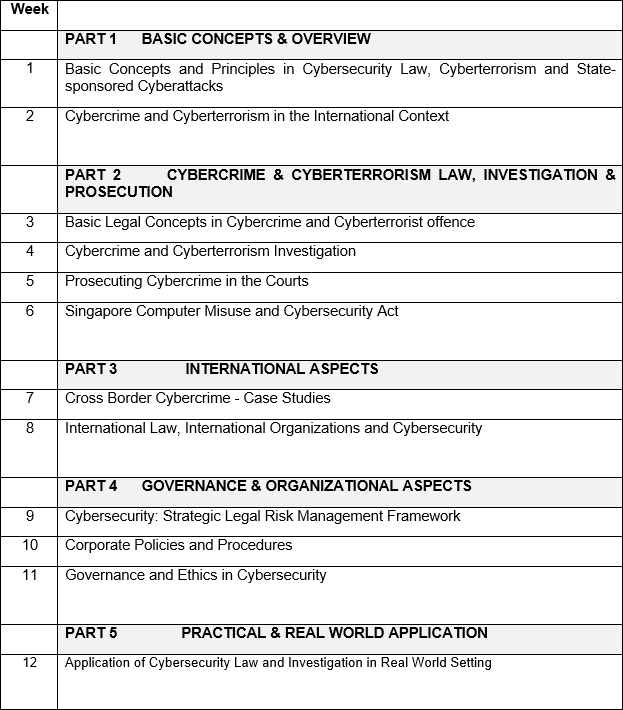
This course will equip students with the knowledge and skills to deal with cybersecurity attacks from the legal, investigative, risk management and policy aspects. It will introduce the concepts and principles of computer crime laws and regulations, cyberterrorism and policy principles and practices to counter cyberthreats.
Course Objectives
By the completion of this subject, the student should be able to understand:
Course Structure
 Recommended text book:
Recommended text book:
Public International Law of Cyberspace
by Kriangsak Kittichaisaree
https://www.springer.com/gp/book/9783319546568
This course examines the international legal regulation of both the conduct of States among themselves and conduct towards individuals, in relation to the use of cyberspace. The course introduces the perspectives of various stakeholders and the challenges for international law. The course discusses state responsibility and key cyberspace rights issues, and addresses cyber warfare, espionage, crime and terrorism. The course also covers the situation of non-State actors and quasi-State actors (such as IS, or ISIS, or ISIL) and concludes with a consideration of future prospects for the international law of cyberspace. Course participants may explore international rules in the areas of jurisdiction of States in cyberspace, responsibility of States for cyber activities, human rights in the cyber world, permissible responses to cyber attacks, and more.
Other topics addressed include the rules of engagement in cyber warfare, suppression of cyber crimes, permissible limits of cyber espionage, and suppression of cyber-related terrorism. The course feature explanations of case law from various jurisdictions, against the background of real-life cyber-related incidents across the globe. With the textbook written by an internationally recognized practitioner in the field, the course objectively guides course participants through on-going debates on cyber-related issues against the background of international law.
This course will appeal to a wide audience, from international lawyers to students of international law, military strategists, law enforcement officers, policy makers and the lay person.
Course Outline

At FutureLaw.ai, our learning strategy emphasises experiential, performance-based, adaptive and agile learning which we term PEbAAL (Performance-based, Experiential, Adaptive, Agile Learning).
The PEbAAL pedagogy will be applied across all our learning platforms that integrates content, pedagogical strategies and real world lifelong learning. For example, when a student learns either through face to face learning, e-learning or hybrid learning, the learning experience will go beyond the classroom and into the workplace.
We require our students to be exposed to real world setting from the time they start school and continuing their lifelong learning journey. Likewise, when a practising lawyer, in-house counsel or business executive learns through our platform, the emphasis is on real world experience that would boost corporate or organizational performance.
The PEbAAL pedagogy works this way:
Using design thinking methodology, we start by identifying the problem to be solved or the value to be created.
We carry out a user needs analysis to figure out what needs to be done in order to solve a problem or create value.
If a problem can be solved through learning and development, we then develop a learning roadmap geared towards solving the problem.
If the problem cannot be solved through learning problems (for example, personality clashes), we do not proceed with the PEbAAL approach but attempt to solve the problem through face to face human interactions.
The learning roadmap will comprise the following elements:
a. Problem identification
b. User needs analysis
c. Learning strategy design which will focus on adaptive and agile learning
d. Tailored learning contents directed at problem solving
e. Integrated learning and development platform backed by a learning and training management system
f. Evaluation framework using the updated Kirkpatrick evaluation methodology
g. Review and refinement to ensure that the organizational KPIs (key performance indicator) are met
Academic institutions are encouraged to create a student e-Portfolio that would capture the students’ learning experiences which they can share with their future employers or partners.
Organizations that require support to create these cloud based e-Portfolio can contact us.
Organizations and enterprises are also encouraged to create their own Skills Portfolio for their employees and this can be connected with our knowledge and skills bank that is constantly updated as part of our adaptive and agile learning.

We develop comprehensive AI-enabled product and service to enable enterprises,
organizations and governments to achieve improved efficiencies, cost optimization,
enhanced brand perception and promote greater customer centricity.
We develop for our partners and clients:
AI-Enabled Dashboard as a centralized platform with interactive dashboards for real-time insights and decision-making.
API Gateway for easy integration with existing enterprise systems and third-party applications.
Security and Compliance measures and compliance with data protection regulations.
We work with our partners and clients to design and develop:
Large Language Models (LLMs): We utilize state-of-the-art LLMs like GPT-4 for natural language understanding and generation.
Machine Learning Algorithms: Implement ML algorithms for data analysis, predictive analytics, and anomaly detection.
Computer Vision: Employ computer vision algorithms for image and video analysis.
Cloud Infrastructure: Utilize scalable cloud platforms like AWS, Azure, or Google Cloud for processing and storage.
IoT Integration: Incorporate IoT sensors and devices for data collection and real-time monitoring.
API Documentation: We provide comprehensive API documentation to assist developers in integrating with your AI-powered solutions.
Developer Support: We offer developer support and forums to address technical queries and issues.
Scalability: We help ensure APIs are designed for scalability to accommodate increasing demand.
Data Collection and Integration: We develop processes to gather data from various sources within the enterprise, including operational data, customer data, and market data.
Data Preprocessing: We support our partners and clients to clean, normalize, and transform data to make it suitable for analysis.
Predictive Modeling: We help build machine learning models for demand forecasting, quality control, and resource allocation.
Customer Feedback Loop: We establish a process for continuous feedback analysis from customer interactions to enhance product/service offerings.
Optimization Framework: We help implement algorithms for resource optimization, supply chain management, and pricing strategies.
Agile Development: We support our partners and clients to adopt agile methodologies for software development to respond quickly to changing market demands.
We work with our partners and clients to manage the following:
Data Lake and Data Warehouse: Store and manage data in a centralized data lake or data warehouse for easy access and analysis.
Data Quality Assurance: Implement data quality checks and data governance practices to ensure data accuracy.
Data Analytics: Utilize data analytics tools for in-depth analysis of historical and real-time data.
Data Monetization: Explore opportunities to monetize data by offering insights to partners or customers.


We work with our partners and clients on strategies and programs on:
How to use AI to personalize customer experiences and recommendations.

How to implement AI-driven chatbots and virtual assistants to enhance customer support.

How to analyze customer sentiment through NLP to improve products and services.

How to create a feedback loop with customers to iterate and enhance offerings.


We work with our partners and clients to develop talents on:


To contact us regarding our offerings, email Zaid Hamzah (Mr),
our Founder, at [email protected].